Windows update against wanna cry virus. The WannaCry ransomware virus has blocked your PC! How to protect yourself from infection? How to decrypt and recover files after the CRYPTED000007 virus
May 19, 2017 7536In I talked about the new WannaCry virus, which infects Microsoft Windows (XP, 7, 8, 10) and how to protect yourself from it. In particular, this is the installation of an update patch that closes a gap in the Microsoft Windows operating system (XP, 7, 8, 10), as well as updating anti-virus databases.
For a home user, there is enough information about WannaCry, since he only needs to download and install the update patch once and that’s it. But, if you are an IT specialist serving an organization with a different number of workstations, then the update installation process needs to be automated.
Of course, you can configure the operating system to automatically update and wait until it installs all the updates. But this process is quite long and requires a large number of reboots of the end workstation, which is not particularly convenient for the user. In any case, automatic updating is worth setting up, but first you need to first download and install the patch update that closes this security hole.
Moreover, some users write that this update may not be installed automatically. But it will not be installed for Windows XP, since this OS is no longer supported by Microsoft.
Therefore, we will forcefully install the MS17-010 update, and in order to do this as quickly as possible and on all computers at once, we will use group policies.
The network in which we will perform all further actions was created during the completion of the video course "" and the course on "
First, it is important that the WannaCry ransomware only exists for Windows. If your device uses macOS, iOS, Android, Linux, or anything else as its operating system, then this malware does not pose a threat to it.
But for Windows devices it does. But different versions of Windows require different patches. So before you install anything, you need to figure out what version of Windows you have.
This is done like this:
- Press the keys and [R] on your keyboard at the same time.
- In the window that appears, enter winver and click OK.
The window that appears will indicate the Windows version.
2. Install patch MS17-010, which closes the Windows vulnerability
When you click on the desired link, an executable file with the MSU extension with the necessary update will be downloaded. Click on it and then follow the prompts of the installation wizard. After installation is complete, reboot the system just in case. Done - the vulnerability is closed, WannaCry won’t just get into your computer.
3. Check your computer for viruses
It's possible that WannaCry managed to get onto your computer before you closed the vulnerability. So, just in case, you should check your computer for viruses.
If you do not have an antivirus, then download a free 30-day version of Kaspersky Internet Security. If you already have a Kaspersky Lab security solution installed, do this.
- Make sure you have the Activity Monitor module enabled. To do this, go to the settings, select the Protection section and make sure that it says On next to the Activity Monitoring item.
- Run a quick scan of your computer for viruses. To do this, in the interface of the anti-virus solution, select the Scan section, in it select the Quick scan item, and then click Run scan.
- If the antivirus detects malware with the verdict Trojan.Win64.EquationDrug.gen, it must be removed and then restarted.
That's it, you are protected from WannaCry. Now take care of family and friends who don't know how to protect their devices themselves.
Hi all! More recently, the Internet was agitated by an event that affected the computers of many companies and private users. This is all due to the emergence of the Wanna Cry virus, which in a short time quickly penetrated and infected a huge number of computers in different countries of the world. Currently, the spread of the virus has decreased, but has not stopped completely. Because of this, users periodically fall into its trap and do not know what to do, since not all antivirus programs are able to neutralize it. According to preliminary data, more than 200 thousand computers around the world were attacked. The Wanna Cry virus can rightfully be considered the most serious threat of the current year, and perhaps your computer will be next on its path. Therefore, let's take a closer look at how this malicious code spreads and how you can fight it.
What kind of villain is the Wanna Cry virus?
“Vona Krai,” as Russian users also call this virus, refers to a type of malware that settles on a computer like a Trojan and begins to extort money from the PC user. The principle of its operation is this: a banner appears on the computer desktop, which blocks all the user’s work and invites him to send a paid SMS message to remove the blocking. If the user refuses to pay the money, the information on the computer will be encrypted without the possibility of recovery. Typically, if you don't take any action, you can say goodbye to all the information stored on your hard drive.
In fact, the Wanna Cry virus can be classified as a group of viruses, ransomware blockers, which periodically fray the nerves of many users.
How does the new pest work?
Once on the computer, it quickly encrypts the information located on the hard drive.
After this, a special message appears on the desktop, in which the user is asked to pay 300 US dollars for the program to decrypt the files. If the user thinks for a long time and the money does not arrive in the special Bitcoin electronic wallet, then the ransom amount will double and he will have to pay 600 dollars, which is about 34,000 thousand rubles in our money, a decent amount, isn’t it?
After seven days, if the user does not send a reward to decrypt the files, those files will be permanently deleted by the ransomware.
The Wanna Cry virus can work with almost all modern file types. Here is a small list of extensions that are at risk: .xlsx, .xls, .docx, .doc, .mp4, .mkv, .mp3, .wav, .swf, .mpeg, .avi, .mov, .mp4, .3gp, .mkv, .flv, .wma, .mid, .djvu, .png, .jpg, .jpeg, .iso, .zip, .rar.
As you can see, this small list contains all the popular files that the virus can encrypt.
Who is the creator of the Wanna Cry virus?
 According to the National Security Agency of the United States of America, a program code called “Eternal Blue” was previously discovered, although information about this code was hidden for use in personal interests. Already in April of this year, the hacker community published information about this exploit.
According to the National Security Agency of the United States of America, a program code called “Eternal Blue” was previously discovered, although information about this code was hidden for use in personal interests. Already in April of this year, the hacker community published information about this exploit.
Most likely, the creator of the land used this code to write a very effective virus. At the moment, it has not yet been established who the main author of the ransomware is.
How does the Wanna Cry virus spread and get onto your computer?

If you have not yet fallen into the trap of the Wanna Cry virus, then be careful. It is distributed most often through emails with attachments.
Let's imagine such a situation! You receive an email message, perhaps even from a user you know, which contains an audio recording, video clip or photo. Having opened the letter, the user happily clicks on the attachment, not noticing the fact that the file has the exe extension. That is, in essence, the user himself starts installing the program, as a result of which the computer files become infected and, using malicious code, a virus is downloaded that encrypts the data.
Note! You can infect your computer with the Vona Krai blocker by downloading files from torrent trackers or by receiving a personal message on social networks or instant messengers.
How to protect your computer from the Wanna Cry virus?
Probably, a reasonable question has arisen in your head: “How to protect yourself from the Wanna Cry virus?”
Here I can offer you several basic methods:
- Since Microsoft developers were seriously worried about the actions of the virus, they immediately released an update for all versions of the Windows operating system. Therefore, in order to protect your PC from this pest, you urgently need to download and install a security patch;
- Carefully monitor what letters you receive by email. If you receive a letter with an attachment, even from an addressee you know, then pay attention to the file extension. Under no circumstances, do not open downloaded files with the extension: .exe; .vbs; .scr. The extension can also be disguised and look like this: avi.exe; doc.scr ;
- To avoid falling into the clutches of a virus, enable the display of file extensions in the operating system settings. This will allow you to see what type of files you are trying to run. The type of masked files will also be clearly visible;
- Installing even L itself will most likely not save the situation, since the virus uses operating system vulnerabilities to access files. Therefore, first of all, install all updates for Windows, and then install ;
- If possible, transfer all important data to an external hard drive. This will protect you from losing information;
- If fortune has turned its back on you and you have fallen under the influence of the Wanna Cry virus, then in order to get rid of it, reinstall the operating system;
- Keep the virus databases of your installed antiviruses up to date;
- I recommend downloading and installing the free Kaspersky Anti-Ransom ware utility. This utility allows you to protect your computer in real time from various ransomware blockers.
Windows patch from Wanna Cry to keep your computer from getting sick.

If your computer has an operating system installed:
- Windows XP;
- Windows 8;
- Windows Server 2003;
- Windows Embedded
Install this patch, you can download it from the link on the official Microsoft website.
For all other versions of the Windows operating system, it will be enough to install all available updates. With these updates you will close the holes in the Windows security system.
Removing the Wanna Cry virus.
To remove ransomware, try using one of the best malware removal utilities.
Note! After the antivirus program runs, encrypted files will not be decrypted. And most likely you will have to remove them.
Is it possible to decrypt files yourself after Wanna Cry.

As a rule, ransomware blockers, which include our “over the edge”, encrypt files using 128 and 256 bit keys. At the same time, the key for each computer is unique and is not repeated anywhere. Therefore, if you try to decrypt such data at home, it will take you hundreds of years.
At the moment, there is not a single Wanna Cry decryptor in nature. Therefore, no user will be able to decrypt files after the virus is running. Therefore, if you have not yet become a victim of it, I recommend taking care of the security of your computer; if you are unlucky, then there are several options for solving the problem:
- Pay the ransom. Here you give money at your own peril and risk. Since no one guarantees you that after you send the money, the program will be able to decrypt all the files back;
- If the virus has not bypassed your computer, then you can simply disconnect the hard drive and put it on a distant shelf until better times, when a decryptor appears. At the moment, it does not exist, but most likely it will appear in the near future. I want to tell you a secret that decryptors are developed by Kaspersky Lab and posted on the No Ramsom website;
- For users of licensed Kaspersky antivirus, it is possible to apply to decrypt files that were encrypted by the Wanna Cry virus;
- If there is nothing important on your PC’s hard drive, then feel free to format it and install a clean operating system;
Wanna Cry virus in Russia.

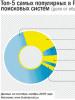
I present a graph that clearly shows that the largest number of computers were affected by the virus on the territory of the Russian Federation.
Most likely, this happened because Russian users do not particularly like to buy licensed software and most often use pirated copies of the Windows operating system. Because of this, the system is not updated and remains very vulnerable to viruses.
Such computers were not spared by the Wanna Cry virus. I recommend installing a licensed version of the operating system and not turning off automatic updates. 
By the way, not only the computers of private users were affected by the “Vona Krai” blocker, but also government organizations such as the Ministry of Internal Affairs, the Ministry of Emergency Situations, the Central Bank, as well as large private companies such as the cellular operator Megafon, Sberbank of Russia and Russian Railways "
As I said above, it was possible to protect yourself from the penetration of the virus. So back in March of this year, Microsoft released Windows security updates. True, not all users installed it, which is why they fell into a trap.
If you are using an old version of the operating system, then be sure to download and install the patch that I wrote about in the paragraph above.
Let's summarize.
In today's article we talked to you about the new Wanna Cry virus. I tried to explain in as much detail as possible what this pest is and how you can protect yourself from it. Also, now you know where you can download a patch that will close holes in the Windows security system.
A computer virus under the original name Wanna Crypt (I want to encrypt) and the appropriate abbreviated name WannaCry (I want to cry) blocked tens of thousands of computers around the world on May 12, 2017. The very next day the epidemic was stopped. However, the developers of the virus made changes to the code, and millions of computers with the Windows operating system were again under attack.
The virus encrypts files and demands a ransom of $300. Victims have already donated tens of thousands of dollars, but there is no information about decryption yet. In any case, it is better to prevent infection and possible consequences than to try to save information after an attack.
1. Install Windows updates
Download from https://technet.microsoft.com/library/security/MS17-010 and install the patch to protect against WannaCry. Microsoft considers this so important that they even released a version for Windows XP (support for which was discontinued in 2014).
In addition, the vulnerability on which the WannaCry attacks are based was fixed in a regular Windows update back in March. Update Windows.
2. Back up important files
Save your work and personal files. You can copy them to an external hard drive or flash drive, upload them to the cloud, upload them to an FTP server, or email them to yourself, a colleague, or a friend. Just don’t overwrite recently saved “clean” files with their encrypted versions. Use other media. It's better to have two copies than none.
3. Close ports 139 and 445
It sounds like something out of a hacker movie, but it's not that difficult. And it is very useful because it will protect your computer from WannaCry. You need to do the following:
- Open the Windows Firewall (Firewall) - for example, through “Network Connections”;
- Select “Advanced Settings”;
- Find “Rules for incoming connections” (Inbound rules) - in the middle of the screen, scroll down a little;
- Then, starting from the main menu: “Action / New rule... / Port / Specified local ports – 139 / Block the connection”;
- similarly for port 445.
4. Find a network administrator or Google it yourself
The main thing has already been done, you are relatively safe. You also need to block SMB v1, inspect the VPN settings, and check the system for viruses. In principle, it’s possible to do all this yourself. But it will be easier and more reliable to find specialists.
5. If you cannot complete at least steps 1-2, turn off the computer
If for some reason you were unable to install a patch from Microsoft, update Windows and save important files on external media, it is better to turn off your computer. Just turn off the power so that the virus has no chance to destroy your digital assets. As a last resort, at least turn off Internet access.
Wait for specialists to arrive, for the release of a decryptor, special versions of “one-click” antiviruses. This will not take much time, but will save years of work spent on creating all those files that are now at risk.